Contents
Changing the MAC Address can help you bypass certain network restrictions by emulating an unrestricted MAC Address or by spoofing a MAC address that is already authorized. For example, a WiFi network may allow only authorized computers to connect to the network and filters out computers based on the MAC address..
Is MAC spoofing the same as ARP poisoning?
The terms ARP Spoofing and ARP Poisoning are generally used interchangeably. Technically, spoofing refers to an attacker impersonating another machine’s MAC address, while poisoning denotes the act of corrupting the ARP tables on one or more victim machines.
What is the difference between IP spoofing and MAC spoofing?
IP address spoofing is very similar to MAC address spoofing, except with IP address spoofing, you’re taking the IP address of another device, or you’re pretending to be a device that isn’t even on your network. This may be something completely legitimate.
What is the difference between MAC flooding and MAC spoofing?
All MAC flooding tools force a switch to “fail open” to later perform selective MAC spoofing attacks. A MAC spoofing attack consists of generating a frame from a malicious host borrowing a legitimate source MAC address already in use on the VLAN.
What is the difference between ARP spoofing and IP spoofing?
ARP spoofing – Links a perpetrator’s MAC address to a legitimate IP address through spoofed ARP messages. It’s typically used in denial of service (DoS) and man-in-the-middle assaults. IP address spoofing – Disguises an attacker’s origin IP. It’s typically used in DoS assaults.
What is the difference between ARP poisoning and MAC flooding?
MAC address flooding is an attempt to redirect traffic to a single port by associating that port with all MAC addresses in the VLAN. C. ARP spoofing attacks are attempts to redirect traffic to an attacking host by sending an ARP packet that contains the forged address of the next hop router.
How does Mac flooding work?
How Does MAC Flooding work? MAC flooding happens when the attacker tries to send numerable invalid MAC addresses to the MAC table. It floods the source table with the invalid MAC addresses. Once the MAC table reaches the assigned limit of the MAC table, it starts to remove the valid MAC addresses.
Can you mimic an IP address?
IP spoofing enables an attacker to replace a packet header’s source IP address with a fake, or spoofed IP address. The attacker does this by intercepting an IP packet and modifying it, before sending it on to its destination.
Is spoofing easy? It all starts with “spoofing” a number — a tactic of changing the phone number seen on a caller ID — and we found it’s surprisingly easy to do.
Can I change MAC address of my phone?
One way to ensure your privacy and security is to change your MAC address. If you have a rooted Android device, you can change your MAC address permanently. If you have an older, unrooted device, you may be able to temporarily change your MAC address until your phone is rebooted.
Does a factory reset change your MAC address?
No MAC address is a physical number built into the hardware of every connected device and is unique. There are spoofing software tools available but resetting a router won’t change that number.
How can I change my MAC address without root?
How can I change MAC address on Android devices without Root?
- Open up settings and then go to WiFi.
- Now, you will see a gear on the top of this screen, click it.
- Voila !
- In order to get the interface name, you will have to install Terminal Emulator for Android.
- Once you download it, install it and open up.
Can I access a device by MAC address?
How can I access a device by MAC address? The easiest way to access a device, knowing the MAC address is to use the arp -a command to find the related IP address. With this address, you can access the device using Remote Desktop Management, a Telnet program, or some other connection facility.
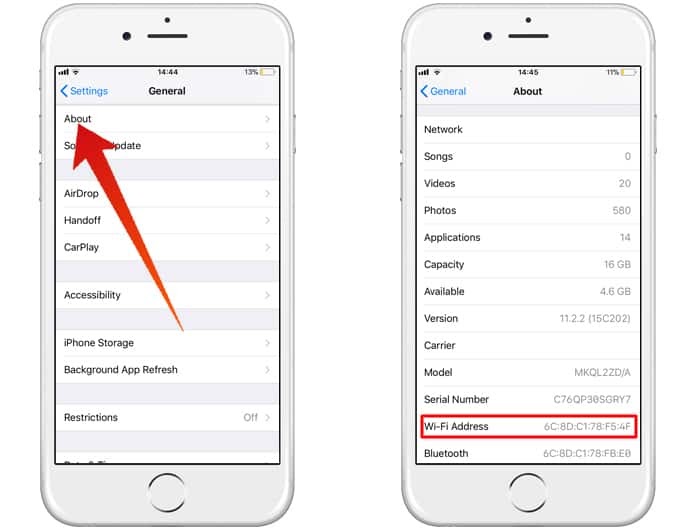
What is the MAC address on my iPhone?
Open the Settings app and navigate to Settings > General > About and scroll to the network section of the page. You’ll find your iPhone’s MAC address in the Wi-Fi Address field.
Which device in the network can read MAC address? A media access control address (MAC address) is a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment.
What can you access with MAC address? Wireless access points often use MAC addresses for access control. They only allow access for known devices (MAC address is unique and identifies devices) with the correct passphrase. DHCP servers use the MAC address to identify devices and give some devices fixed IP addresses.
How do I ARP a MAC address? To see all the MAC addresses and their associated IP addresses, type “arp -a”. This command will list all the available MAC addresses in the system. The address on the left is the IP address, while the right is the MAC address. Find the corresponding IP address for the specific MAC address you want.
Does VPN change MAC address?
There is no difference between the MAC address assigned by the manufacturer of your device as well as its identity and being changed by the VPN. Your location details are hidden by a VPN provider. For you to connect to the internet, your MAC address must be visible.
Does a website know your MAC address?
Websites can’t see your MAC address at all, so you don’t need to use a VPN.
How do I hide my MAC address on my phone?
Turn Private Address off or on for a network
- Open the Settings app, then tap Wi-Fi.
- Tap the information button next to a network.
- Tap to turn Private Address on or off. If your device joined the network without using a private address, a privacy warning explains why.
Can you be tracked by your MAC address?
The short answer is no. You could not even do anything with knowing the MAC address of someone’s local computer protected behind a router.
Is IP spoofing illegal?
Is IP Spoofing Illegal? IP spoofing is illegal in many countries. A variety of government agencies, including the FBI and NSA, monitor traffic as a means to identify potential threats against computer systems. This includes any forged packets or other efforts to disguise IP addresses.
Why is MAC spoofing a wireless threat?
A MAC spoofing attack is where the intruder sniffs the network for valid MAC addresses and attempts to act as one of the valid MAC addresses. The intruder then presents itself as the default gateway and copies all of the data forwarded to the default gateway without being detected.
How can spoofing be prevented?
IP spoofing protection for end users:
Avoid carrying out transactions such as shopping or banking on unsecured public Wi-Fi. If you do need to use public hotspots, maximize your safety by using a virtual private network or VPN. A VPN encrypts your internet connection to protect the private data you send and receive.
What is Mac clone in router? Basically, if you tell your router to clone your network card’s MAC Address. It makes your ISP think that you’re still using the same computer/network card/device to access their services, and therefore they allow your router on the network.